Don't Buy Antivirus, Use an LLM instead
What if your LLM could protect your system the same way it helps you write code or summarize documents?
LLMs are probably the cleanest interface we’ve ever had for computers. You say what you mean; the model turns it into actions. Local LLMs are the next operating systems. Instead of installing traditional software, you’ll install “skills” or add-ons on your LLM of choice. The LLM becomes the runtime. That opens an interesting question: could you extend the skills of your LLM and turn it into an antivirus? Not a static scanner but an antivirus that reasons, similar to having a malware analyst by your side.
The answer is simple. We can supply the LLM with a set of “skills” or tools to allow it to reason about malware. Here is a demo:
However, LLMs can handle text/code and other modalities but not binaries. So we first need to analyze malware and then the LLM can reason about the textual analysis reports. Human malware analysts usually rely on two types of analysis: static and dynamic analysis. Static analysis refers to all the analysis we can perform without executing an unknown software sample, while in dynamic analysis we execute the sample in a safe environment (usually a VM) and monitor the software’s behavior. Static analysis is fast and computationally cheap, so it is more practical in an antivirus context. Additionally, malware analysts correlate their results with other analysts’ findings by sharing threat intelligence. For our antivirus LLM we will implement tools to allow it to perform all types of analysis and query a popular threat intelligence service, VirusTotal.
To implement the tools we will employ MCP, a protocol for connecting AI apps to external tools and systems. That means that we can implement a set of tools once and then be able to use it with any LLM.
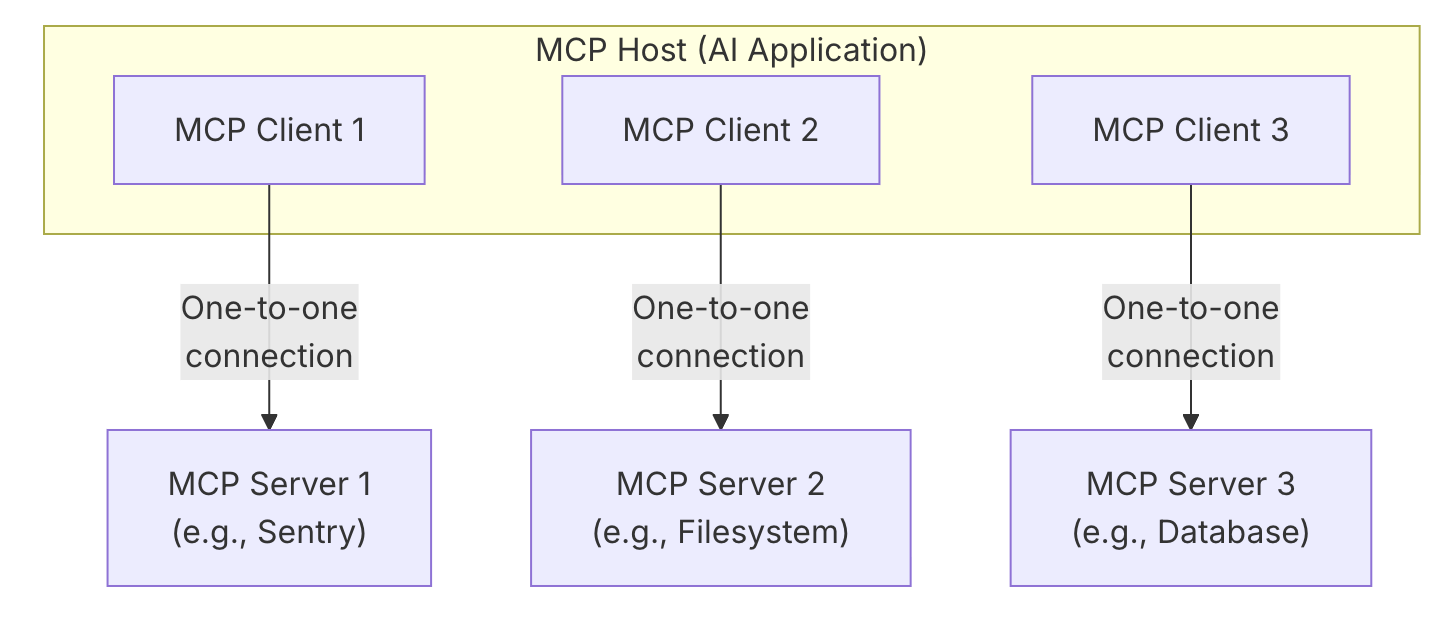
For static analysis we will implement the following tools:
- Get the SHA256 hash of a file
- Determine its type
- Calculate its Shannon entropy
- Extract the printable strings inside the file
- Analyze it with a well-known tool CAPA
Defining a tool is as simple as this:
@mcp.tool()
async def get_file_hash(filepath):
"""
Get the SHA256 hash of a file.
Args:
filepath: The file path to analyze
Returns:
The SHA256 hash of the file as a string
"""
sha256_hash = hashlib.sha256()
async with aiofiles.open(filepath, 'rb') as f:
while True:
byte_block = await f.read(4096)
if not byte_block:
break
sha256_hash.update(byte_block)
return sha256_hash.hexdigest()
For dynamic analysis we will use Hybrid-Analysis, a popular sandbox offering. A very simple implementation of the MCP server for testing can be found here: https://gist.github.com/gxenos/29d41c18e6245e7c52b2702d7719b2b8 We’ll also be using this toolkit to allow the LLM to query VirusTotal, a threat intelligence service: https://github.com/emeryray2002/virustotal-mcp. VirusTotal also allows you to scan files with multiple traditional AV systems – similar to what the LLM does in the demo video. Finally, we need access to the filesystem. There are many options, for example for Claude Desktop it’s very easy to implement.
Then we can add all MCP servers on Claude.

The LLM can now inspect files, query related tools and reason about intent – it’s already halfway to being a proper antivirus.
Credit: Georgios Xenos, Manolis Tzagakis